Centralised and Secure User and SSH Key Management
Automate and manage your Users and SSH Keys across your infrastructure quickly and easily for increased security and agility.
Features
Benefits
Ease management and increase security by moving to a cloud based SSH key management system.
Ensure Compliance
Align with the industry standard IT Security frameworks including ISO27001, SOC2, PCI-DSS and HIPAA. These intern ensure compliance with data privacy regulations GDPR, CCPA, LGPD and POPIA.
Enforce IT Security Policy
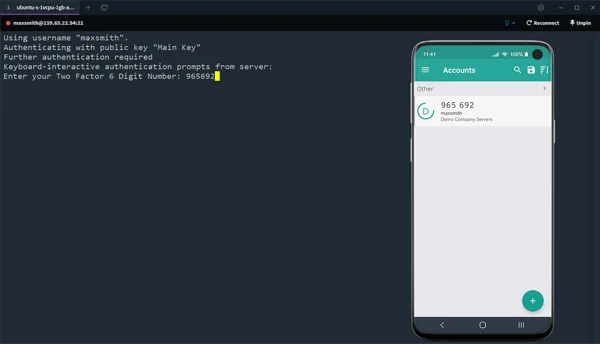
Ensure best practise IT security policies are enforced across your infrastructure. Disable password login and enforce SSH Two Factor Authentication.
Reduce IT Burden
Centralised management of Linux users and SSH keys can reduce the burden on IT teams using custom scripts and automation tools to fill the gap. Onboard users of all skill levels quickly with self-service functionality.
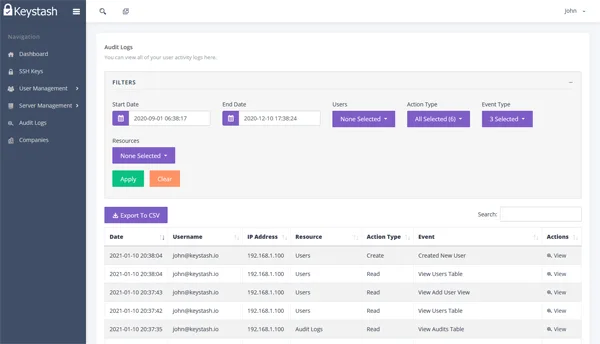
Gain Visibility
Quickly see which servers meet the highest security standards and those that are at risk. Get oversight into who has access to what and who granted that access.
Reduce Costs
Our disruptive pricing enables small and large organizations to level up their Linux security. Our packages grow with you and start with a free tier!
Multi Cloud and Private Cloud Compatible
Keystash works in all clouds and private networks. The Keystash agent communicates with our systems using regular HTTPS outbound connections making firewall setup a breeze. Users can still login to servers even if your connection to the internet is down.
Manage Linux users, SSH keys and SSH Two Factor Authentication
Get up and running quickly with our easy to install agent and take the burden of managing user accounts and SSH policy off your team.
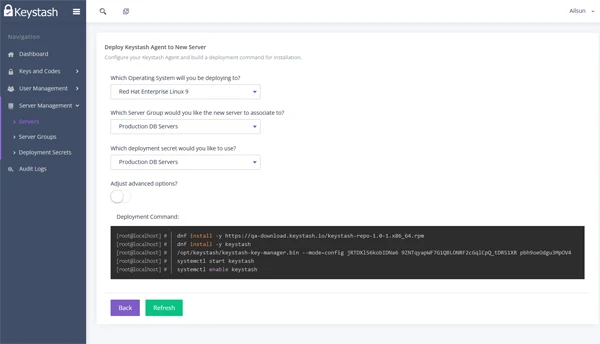
How Keystash works

Install the Keystash Agent on your servers using a simple bash script that can be incorporated into any automation tool (Chef, Ansible...)
Once the agent is running it will register with Keystash and show as a server in your account. The server is now linked to a group of servers ready to be configured.
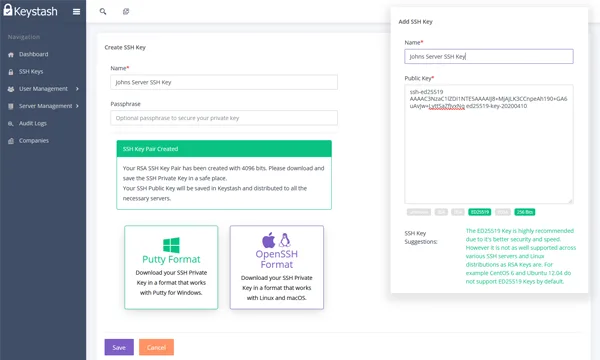
Invite your users and let them upload their SSH Keys.
Keystash can guide new users to create the correct SSH Key or only upload strong keys into the system.


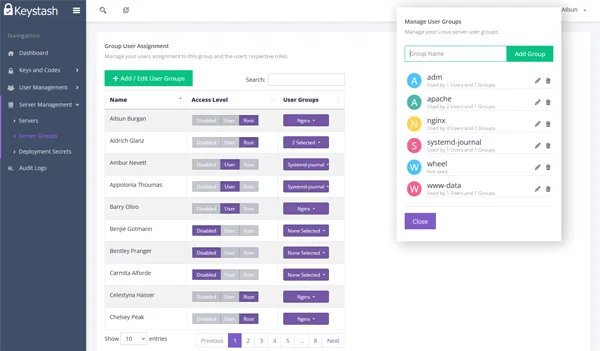
Give users access to Servers
Choose which users have access to the server groups you need. You can give normal user access or SUDO access for higher privileges.
The Keystash Agent synchronises Users and SSH Keys from Keystash servers.
Using an outbound HTTPS connection to Keystash, the agent downloads and creates all new users and copies their SSH Keys to the /{users home directory}/.ssh/authorised_keys file.


Users with "root" permissions will be given "sudo" access on the servers.
Similarly if you remove any users from Keystash, then their account and SSH Keys are removed from all the servers they had access to.
Customer reviews

Keystash
Linux Identity and SSH Key Management
15 Reviews as of March 2023 Submit a review Source: G2.com, Inc.“Keystash solved centralised key management and user management in our Linux environment.
We went with Keystash because we couldn’t find another solution with the same features and the benefit has been the easiest deployment of keys to new servers which saves us time!”
Leejay Tavares (CTO)
1010 Technologies
"I needed a central SSH key management solution with MFA and Keystash was easy to setup and well priced. I have had to use support, as a third party piece of software didn't like the MFA option.
Keystash support was excellent and they helped me to find a way to get it to work as I wanted it to. I no longer have to manage user access for each server, so I save time."
David Eaton (Infrastructure Manager)
Co-operative Web
Frequently Asked Questions
Here are the answers to some of the most common questions we hear from our customers
What Operating Systems does Keystash support?
Keystash supports the most common server Linux distributions including Debian 9 - 11, Ubuntu 18 - 22, RedHat RHEL (incl. clones) 7 - 9 and more.
Can I create a temporary user and SSH key?
Yes. When creating a User simply enable expiration and set the date and time for when the account will expire. This allows you to create accounts for contractors or even regular users who need one time access to a particular system.
What happens if I lose connectivity to Keystash?
The Keystash server agent copies SSH Keys to the local file system on your servers so that users can always login irrespective of whether you server can still communicate with Keystash in the cloud.
Do I need to install software on my servers?
Yes, the Keystash agent will need to be installed on all servers that you want to manage. But don't worry, there are no software dependencies needed to run the agent, just an SSH Server that uses the authorized key files in the users home directories.