Implementing SSH Two-Factor Authentication
SSH Two-Factor Authentication (2FA) is a crucial security measure for protecting your Linux servers. This guide will walk you through the implementation process, highlight best practices, and help you avoid common pitfalls.
Why Implement SSH Two-Factor Authentication?
SSH keys are a secure method of authentication, but they're not infallible. If a private key is compromised, an attacker could gain unauthorized access to your servers. Two-factor authentication adds an extra layer of security by requiring a second form of verification, significantly reducing the risk of unauthorized access even if SSH keys are compromised.
Methods of Implementing Two-Factor Authentication for SSH
There are three main methods to implement two-factor authentication for SSH:
- Time-based One-Time Password (TOTP): Uses an algorithm to generate a one-time password that changes every 30 seconds.
- Universal 2nd Factor (U2F): Uses a physical security key for authentication.
- SMS-based codes: Sends a code via text message (not recommended due to potential security vulnerabilities).
At Keystash, we recommend using TOTP for its balance of security and convenience.
Implementing Two-Factor Authentication with Keystash
Keystash simplifies the process of implementing SSH two-factor authentication across your servers. Here's a step-by-step guide:
- Log in to your Keystash account.
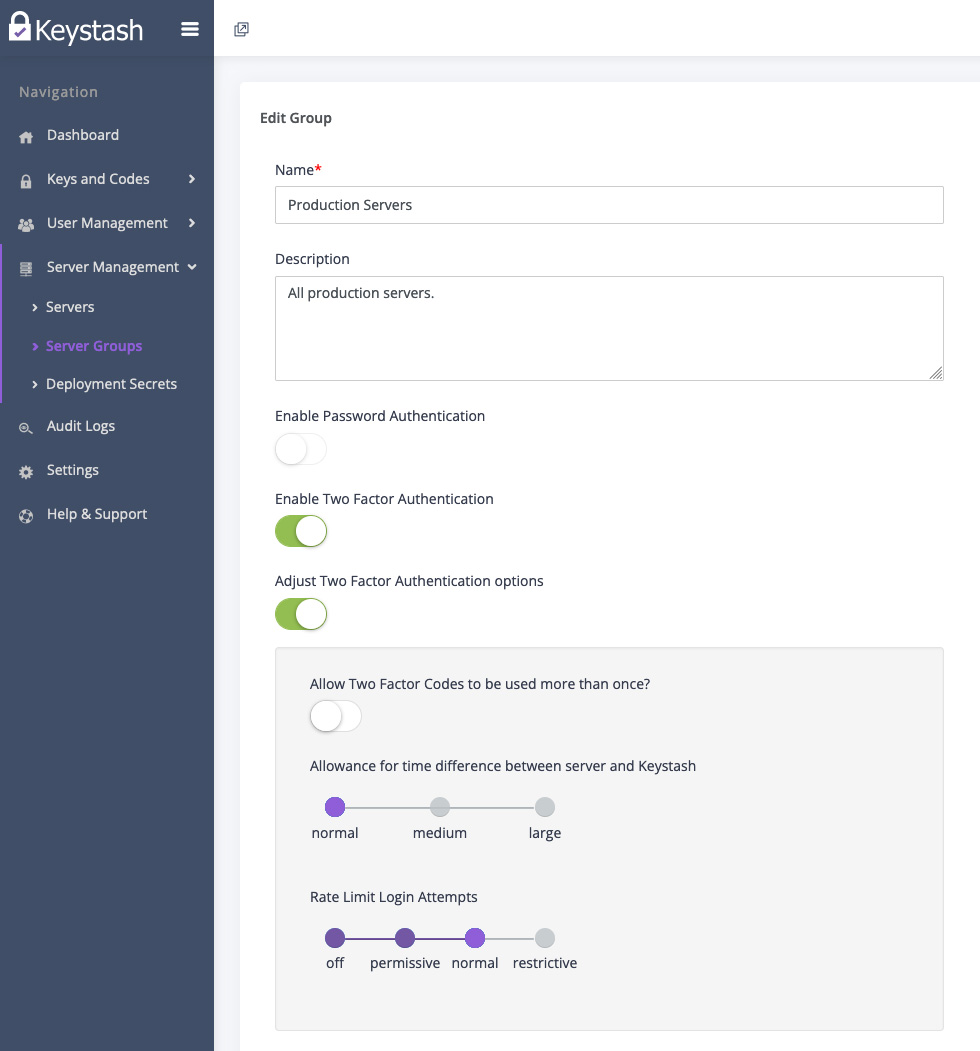
- Navigate to the Server Management section on the main menu. Then click Server Groups
- Select the group of servers where you want to enable two-factor authentication.
- Click on Enable Two-Factor Authentication.
- Click on Adjust Two-Factor Authentication options if you would like to adjust the security level of the two-factor authentication protection.
- Keystash will automatically configure the necessary settings on your servers.
For your users, the process is equally straightforward:
- Users log in to their Keystash account.
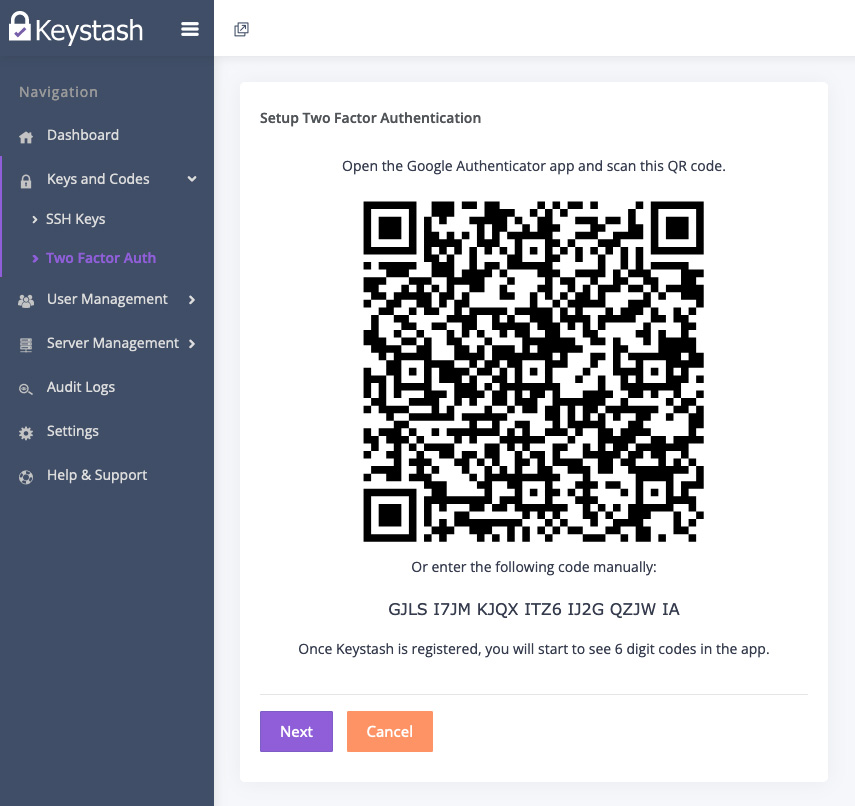
- They navigate to Keys and Codes section on the Main menu. Then they click Two Factor Auth.
- They select Create to start the two-factor authenication setup process.
- They scan the provided QR code with their authenticator app.
- They enter the generated code to confirm setup.
- Finally, they save their backup codes into a secure location.
Best Practices
- Use a reputable authenticator app: We recommend apps like Google Authenticator, TOTP Authenticator, Authenticator Pro or Microsoft Authenticator.
- Generate and store backup codes: Provide users with one-time use backup codes in case they lose access to their authenticator app. Did you know that Keystash allows users to access their backup codes at any time, right from the interface?
- Implement gradually: Roll out 2FA to a small group of users first to identify and resolve any issues before full deployment. Keystash allows users who have not configured two-factor authentication to continue to login even if you have enabled it on the server. This promotes a smooth rollout to your users.
- Educate your users: Ensure all users understand the importance of 2FA and how to use it correctly.
- Regular audits: Periodically review 2FA usage and ensure it's properly configured across all servers. Keystash makes this quick and easy in one central place.
Common Pitfalls and How to Avoid Them
- Lockouts: Ensure there's always a way for authorized users to regain access if they lose their second factor. Keystash provides admin override capabilities for such situations.
- Inconsistent implementation: Use a centralized solution like Keystash to ensure two-factor authentication is consistently implemented across all servers.
- Neglecting backup authentication methods: Always have a fallback method, such as backup codes, to prevent complete lockouts.
- Over-reliance on 2FA: While two-factor authentication significantly enhances security, it's not a silver bullet. Continue to follow other security best practices.
Conclusion
Implementing SSH Two-Factor Authentication is a crucial step in enhancing your server security. By following these best practices and avoiding common pitfalls, you can significantly reduce the risk of unauthorized access to your Linux servers. Keystash simplifies this process, allowing you to implement robust two-factor authentication across your entire infrastructure with ease.
Keystash provides a comprehensive solution for SSH key management and Two-Factor Authentication implementation. Our platform is designed to enhance your Linux server security while simplifying management tasks. Contact us if you need assistance in setting up SSH 2FA or have any questions about our services.
Andrew Burns
Founder, Keystash Limited.Andrew has spent the last 20 years working in IT infrastructure, networks and software development and is a passionate Linux fanboy and security scholar.