How to generate the best SSH keys
It’s common practice for most organisations to use RSA SSH key pairs due to their compatibility across Linux distributions and cloud services. Consider this: the algorithm behind RSA was designed in 1977, at a time when computing power was not what it is today.
This is why you should consider newer SSH key types that have been designed with today's IT security risks in mind. Let's take a look at what's available:
TL;DR (too long; didn't read): We suggest using Ed25119 keys in general unless there are legacy Linux distributions and services you need to make use of. Also ensure you add some small options to key generation processes to make them extra secure. See more detail below.
RSA Keys
This is the default option for ssh-keygen on most Linux distributions and for Puttygen (the most popular Windows key generator). It is still the most widely supported key type, however this is not a reason to skip other newer key types.
The best practice for RSA keys today is to use a key size of 2048 bits or higher, however there are diminishing returns using longer keys (3072 bits and higher). Longer keys take more time to create and there are newer key types that give equivalent and usually better security while being faster to create and smaller in size.
DSA Keys
The OpenSSH server that is the most popular SSH server on Linux distros has deprecated the support of DSA keys as they are generally considered insecure due to discovered vulnerabilities. We suggest you avoid DSA keys if possible.
ECDSA Keys
ECDSA is a variant of DSA keys, however it uses Elliptic-Curve cryptography, which is a newer (at least in comparison to RSA) approach to public-key cryptography, designed in 1985 and its benefits include smaller key size and they are significantly faster to create.
Elliptic-curve cryptography keys or ECC keys provide comparable security to longer RSA key types. For example, a 256-bit ECC key would be comparable to a 3072-bit RSA key.
However, cryptography experts have shared concerns over the trustworthiness of NIST produced curves used in ECDSA and that the NSA may have implemented backdoors. This, together with the technically superior EdDSA (Ed25519) key type, we suggest you avoid ECDSA keys and consider EdDSA key types instead.
EdDSA Keys (Ed25519 & Ed448)
The Edwards-curve Digital Signature Algorithm was designed in 2011 and is highly optimised for x86-64 processors. It provides equivalent and usually better security than ECDSA and longer key length RSA keys.
Its main advantages are small key sizes, fast key generation times, high performance and is resistance against side-channel attacks.
Something to note though is its compatibility. In particular Ed25519 keys are only supported in versions of OpenSSH server 6.5 and higher. Of course, you can always upgrade the version of OpenSSH, however there may be circumstances where this is not possible. The following popular Linux distributions have support for Ed25519 keys out of the box:
- Ubuntu 14.04 and higher
- Debian 8 and higher
- Redhat Enterprise Linux 7 and Higher (including CentOS 7, Oracle Linux 7, Scientific Linux 7)
- RockyLinux and AlmaLinux 8 and higher
- Amazon Linux AMI 2015.09 and higher
- Fedora Server 21 and higher
- Arch Linux since 2016
Note: Amazon AWS EC2 and Google GCP support Ed25519 keys, however Microsoft Azure currently does not support these keys.
Ed448 keys are similar in many ways, however they have not gained widespread adoption, in particular OpenSSH as of 2023 has not implemented this key type citing that Ed25519 already provides all the advantages of ECC keys. Additionally, vulnerabilities were found in SHA-3 in late 2022: (CVE-2022-37454). EdDSA makes the use of SHAKE256 mandatory for Ed448 keys and SHAKE256 is part of the SHA family of standards.
How to generate an EdDSA Ed25519 key
For ssh-keygen simply use the following command:
$ ssh-keygen -o -a 100 -t ed25519
The “-a 100” controls the key derivation function rounds, which controls how difficult it would be to brute force unlocking an encrypted (passphrase locked) private key. A higher number means it would be more secure but would take longer to unlock. Numbers between 80 and 200 are considered sufficiently secure with a low time to unlock.
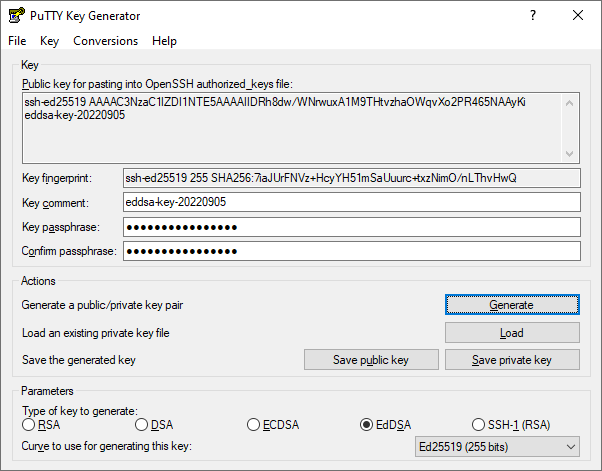
For Puttygen simply select EdDSA and then select “Ed25519 (255 bits)” as per below:
Can Keystash help me implement secure keys?
Keystash is an end-to-end user and SSH key management platform designed to help you and your team better manage and secure SSH keys and SSH servers. Keystash supports all RSA, ECDSA and Ed25519 key types and can help your users generate and implement secure keys. Our system actively warns users when using insecure keys or bad configurations. Additionally, Keystash creates strong and secure SSH keys for your users if they don’t want to use the tools already listed above.
Keystash can help your team transition from RSA to Ed25519 SSH keys by enabling users to have two SSH keys active (RSA and Ed25519 keys) while your legacy systems are being decommissioned. You can remove all RSA keys from Keystash once all RSA only systems have been decommissioned with zero impact on your users connections as the Ed25519 keys would continue to work.
Keystash is ideally suited to bring visibility and control to your Linux environment for businesses of all sizes. Contact us if you would like assistance in setting up an Identity and Access Management and SSH Key management tool.
Andrew Burns
Founder, Keystash Limited.Andrew has spent the last 20 years working in IT infrastructure, networks and software development and is a passionate Linux fanboy and security scholar.